February 24, 2023 | Author: David Perrin
Incorporate ITDR into your organization’s Identity Governance and Administration (IGA) strategy for improved visibility into access and greater management capabilities.
Identity and Access Management (IAM) and ITDR are sibling disciplines. Where IAM solutions ensure that individuals requiring access to resources have that access, ITDR aspires to detect and eliminate risks around identities. If you’re reading this, you are likely familiar with Identity and Access Management (IAM) activities such as access reviews and audits. You may be the person generating routine reports – or you could be the party responsible for forensic discovery of how someone was able to accidentally access a resource which they should have been prevented from accessing.
Those forms of review have critical utility for compliance, process development, testing, and more. That’s important work! With maturing standards, APIs, and cloud technologies, ITDR products are able to support existing IGA activities with real-time (or scheduled) views into access of your on-prem or cloud resources as well as automated and manual control mechanisms.
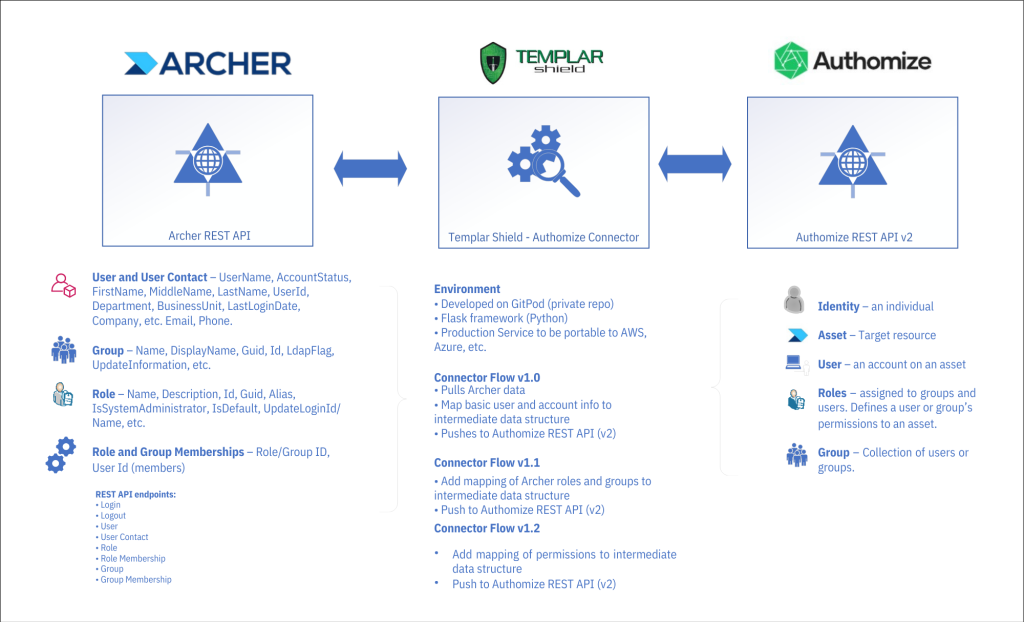
A short time ago, I had the opportunity to develop an integration between a leading enterprise risk management utility (Archer) and Authomize’s cloud-based Identity Threat Detection and Response platform. Our sister practices at Templar Shield have extensive experience with Archer and offered access to the Archer REST API in one of Templar’s test environments.
Authomize has a substantial collection of connectors for integrating popular resources (e.g., Okta, Azure, AWS, Box) and the availability of their REST API presented an opportunity for Templar Shield to develop an integration with Archer. The Authomize team, their API’s maturity, the quality of their API documentation, and our in-house Archer experts at Templar Shield made the task of developing connections between Authomize and Archer an enjoyable exercise.
The approach taken in developing this integration was to:
1. Utilize the REST APIs in Archer and Authomize leveraging their respective endpoints
- Archer and Authomize GET endpoints for retrieving basic identity, group, role, access, and related details
- Authomize POST endpoints for pushing limited identity details, group, role, and permissions
2. Develop a data object mapping model between Archer and Authomize
- Start with Users / Accounts and Applications / Assets
- Add groups, roles, memberships
- Permissions
3. Help an Identity Analyst use Authomize ITDR environment to see who has access to Archer and identify any potential Identity threats
Technical landscape overview
Highlights and challenges during development
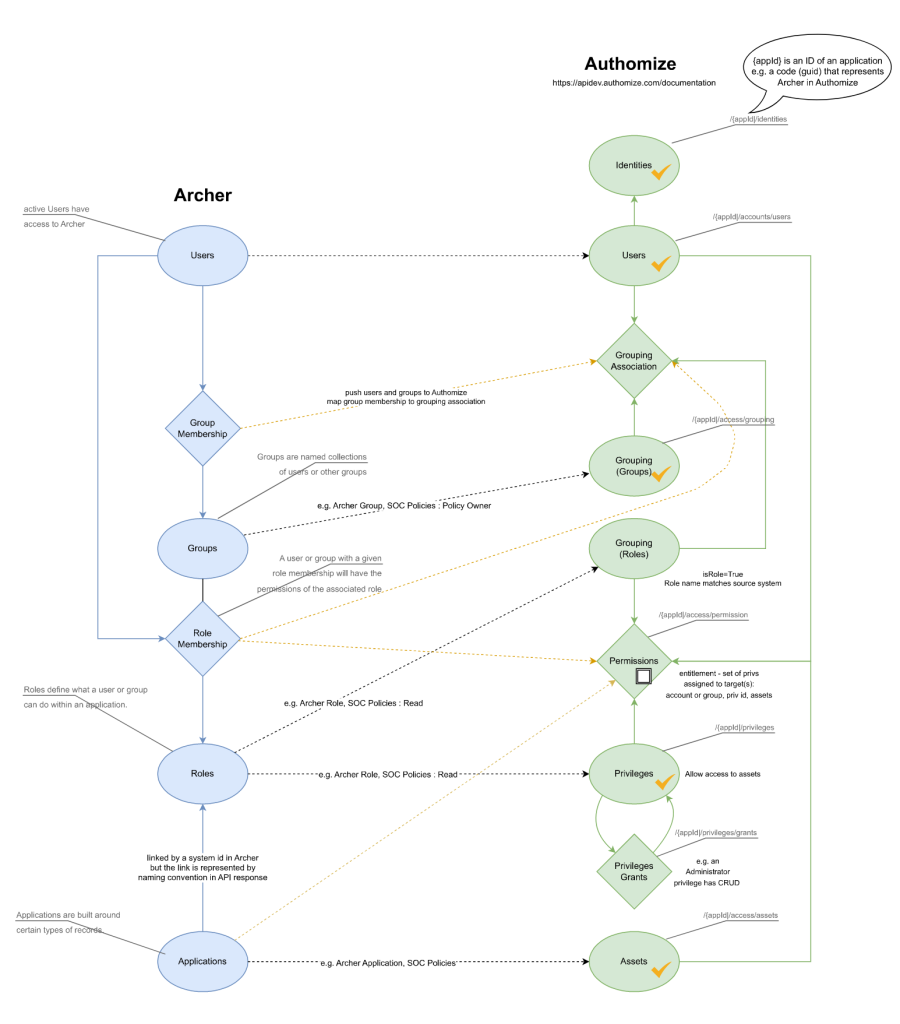
After building out requests in the Postman API client and reviewing responses, I noticed identifier and naming conventions that required additional consideration. Terms like “groups” in Archer have similar but not the same meaning in Authomize. Working out a model which mapped one system to another was critical. Taking a cue from our IAM practice Director on recent work done with the Python-based Flask web framework and the cloud development environment Gitpod, API requests were migrated to a web application which pushed applications (assets), users, groups, roles, and memberships to Authomize. The Archer and Authomize APIs have always been solid and responsive. The integration is now to the point where data passed to Authomize can be used to generate identity and access diagrams within the platform to facilitate Identity Threat and Detection processes.
Data model and object mapping – current state
Summary
Like IAM technologies, ITDR solutions aspire to support a variety of application connectors and integrations. Not all applications are popular enough for technology vendors to develop integration capabilities. Fortunately, Authomize is one ITDR solution which has invested in an API to allow businesses to integrate applications beyond Authomize’s own connectors.
About the Author

David Perrin is an IAM Senior Consultant with Templar Shield. He enjoys learning about customer challenges and helping them achieve their goals. David’s experience includes Enterprise and IAM System Design, application integration, system testing, and assurance. In these capacities, David helps clients realize improved efficiencies, business requirements, and customer experiences. He can be reached at david.perrin@templarshield.com.




