
Third-Party Risk Management Framework

Third-Party Risk Management Framework
April 11, 2023 | Author: Narayanan Rajendran
Today’s third parties require more access to data assets of organizations they do business with and are increasingly working with their own third parties (also known as Nth or Fourth Parties), multiplying the size and complexity of the third-party network. In fact, in the last four years, legal and compliance leaders have classified 2.5X more third parties as high-risk. Gartner’s study on Third-party risk, reveals that twice as many compliance leaders identify third-party risk as a top threat. This is because third-party risks have fundamentally changed. Leaders say they have experienced:
More than 4,100 publicly disclosed data breaches occurred in 2022 exposing approximately 22 billion records (reported by Security Magazine). Every third party an organization is engaging, they must consider various associated third-party risks, including financial risks, reputation, resiliency, information security, cyber security exposures, legal actions or compliance, and performance failures that could ultimately disrupt their organization. Building a comprehensive TPRM Framework is increasingly important as organizations outsource more significant portions of their workloads to third-party suppliers.
Introduction to TPRM frameworks:
Third-party risk management (TPRM) frameworks provide organizations with a roadmap to build their TPRM programs based on industry-standard best practices. Frameworks the foundation of TPRM programs and provide the cornerstone of baseline control requirements for third-party vendors and suppliers.
There is no single approach to developing a TPRM framework, but some commonly used frameworks provide a solid starting point. Frameworks provided by organizations such as the National Institute of Standards and Technology (NIST) and the International Standards Organization (ISO) are a great place to start.
Third-party risk management policies guide organizations in the building, applying, managing, and implementing best practices. When implementing a third-party risk management framework, companies must examine the nature of the risk involved and deal with the changing business, regulatory and legal environments – and their potential impact on the organization’s operation. Effectively utilizing TPRM frameworks will reduce risks to organizations and their customers.
TPRM framework for an organization:
No single framework is likely to provide every organization with every control to comprehensively meet disparate regulatory, risk management, and due diligence objectives and requirements. Many organizations choose to work exclusively with NIST or ISO and draw from multiple frameworks and guidance documents from each of those bodies when developing and maturing their programs.
The following considerations and how they impact your organization are important when selecting a TPRM framework. Understanding the organizational risks is the first step in choosing the proper framework for your company. The infographic below illustrates many of the relevant risk categories
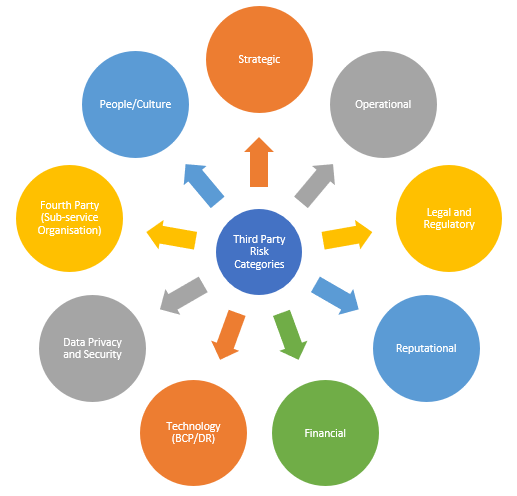
Some vendors or third parties may push back or be reluctant to engage in the assessment of their risk and security posture due to the time, and resources sometimes necessary to satisfy. TPRM isn’t just about ensuring that a partnership does not expose your organization to intolerable risk potential; it is also about rewarding vendors that reduce your organization’s risks through best practices. That’s why it’s important to select the correct TPRM framework and understand its impact on your ecosystem of external vendors.
Aspects that need to be considered to help you build a TPRM Framework:
Understanding the specific business requirements or the risk environment in which the business operates will help an organization build a mature and effective TPRM Framework. Shared Assessments, NIST 800-161, and ISO 27036 can provide specific examples of important SCRM (Supply Chain Risk Management) and TPRM controls, while organizations such as ISACA are valuable knowledge sources of practically applied best practice, third-party risk management processes.
About Author:

Narayanan Rajendran is a Management Consultant and Leads Third Party Risk Managed Services at Templar Shield. He has 15+ years of progressive experience advising global majors/Fortune 500 companies on Governance, Risk Management, and Compliance initiatives.
February 24, 2023 | Author: David Perrin
Incorporate ITDR into your organization’s Identity Governance and Administration (IGA) strategy for improved visibility into access and greater management capabilities.
Identity and Access Management (IAM) and ITDR are sibling disciplines. Where IAM solutions ensure that individuals requiring access to resources have that access, ITDR aspires to detect and eliminate risks around identities. If you’re reading this, you are likely familiar with Identity and Access Management (IAM) activities such as access reviews and audits. You may be the person generating routine reports – or you could be the party responsible for forensic discovery of how someone was able to accidentally access a resource which they should have been prevented from accessing.
Those forms of review have critical utility for compliance, process development, testing, and more. That’s important work! With maturing standards, APIs, and cloud technologies, ITDR products are able to support existing IGA activities with real-time (or scheduled) views into access of your on-prem or cloud resources as well as automated and manual control mechanisms.
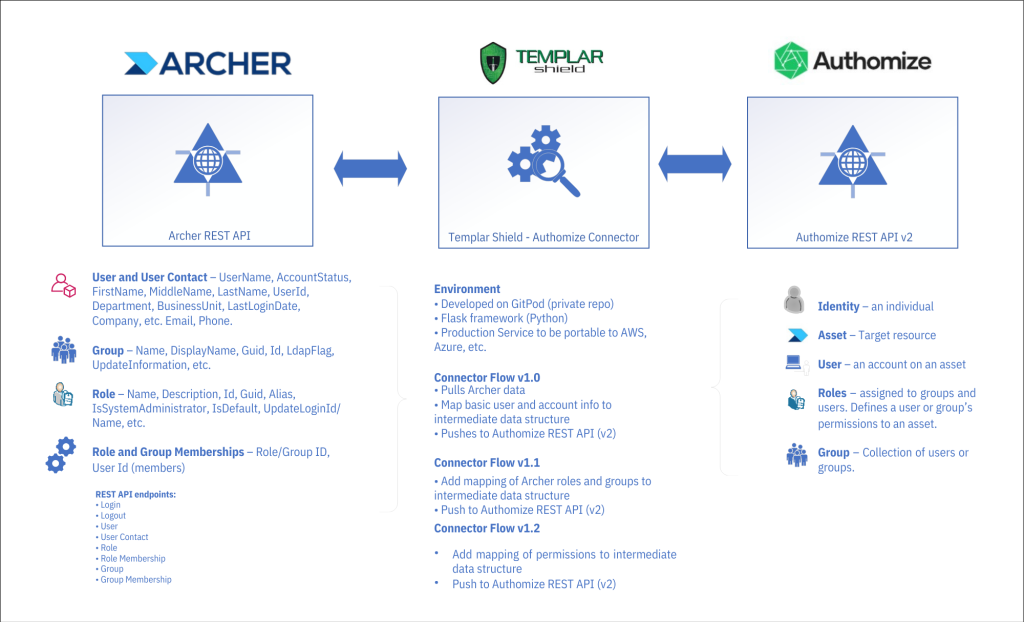
A short time ago, I had the opportunity to develop an integration between a leading enterprise risk management utility (Archer) and Authomize’s cloud-based Identity Threat Detection and Response platform. Our sister practices at Templar Shield have extensive experience with Archer and offered access to the Archer REST API in one of Templar’s test environments.
Authomize has a substantial collection of connectors for integrating popular resources (e.g., Okta, Azure, AWS, Box) and the availability of their REST API presented an opportunity for Templar Shield to develop an integration with Archer. The Authomize team, their API’s maturity, the quality of their API documentation, and our in-house Archer experts at Templar Shield made the task of developing connections between Authomize and Archer an enjoyable exercise.
The approach taken in developing this integration was to:
1. Utilize the REST APIs in Archer and Authomize leveraging their respective endpoints
2. Develop a data object mapping model between Archer and Authomize
3. Help an Identity Analyst use Authomize ITDR environment to see who has access to Archer and identify any potential Identity threats
Technical landscape overview
Highlights and challenges during development
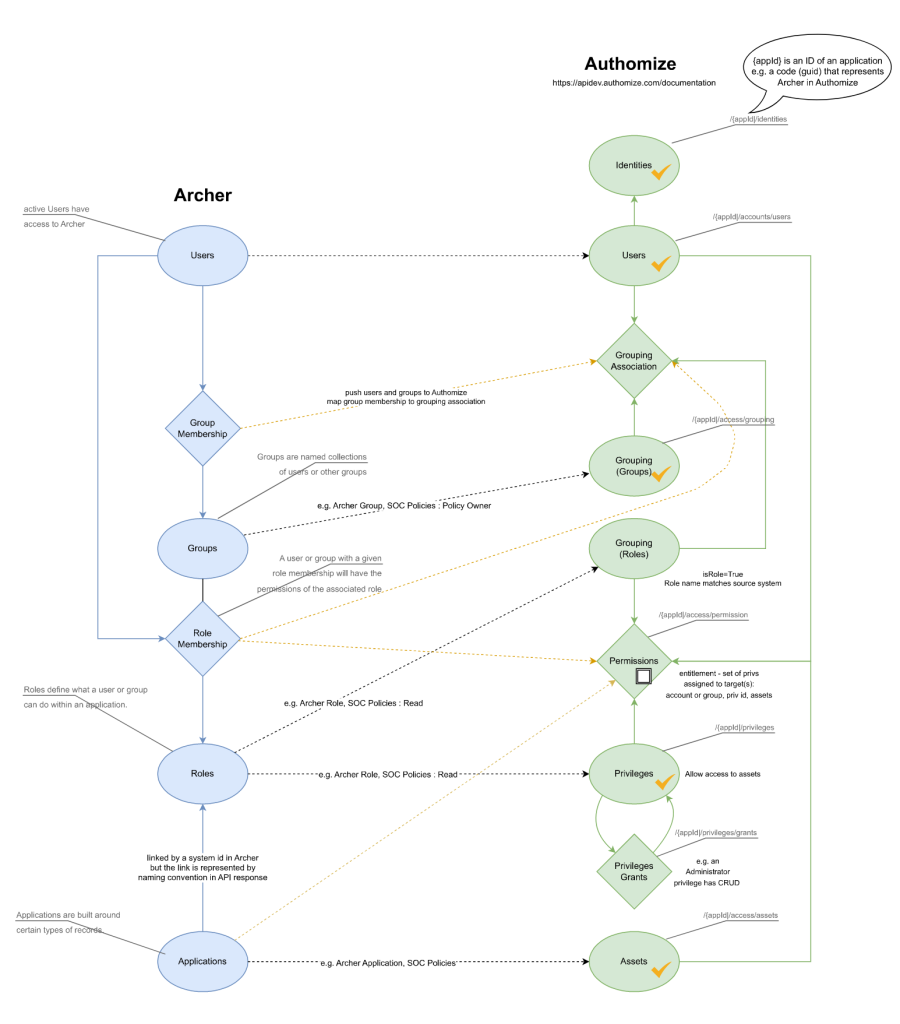
After building out requests in the Postman API client and reviewing responses, I noticed identifier and naming conventions that required additional consideration. Terms like “groups” in Archer have similar but not the same meaning in Authomize. Working out a model which mapped one system to another was critical. Taking a cue from our IAM practice Director on recent work done with the Python-based Flask web framework and the cloud development environment Gitpod, API requests were migrated to a web application which pushed applications (assets), users, groups, roles, and memberships to Authomize. The Archer and Authomize APIs have always been solid and responsive. The integration is now to the point where data passed to Authomize can be used to generate identity and access diagrams within the platform to facilitate Identity Threat and Detection processes.
Data model and object mapping – current state
Summary
Like IAM technologies, ITDR solutions aspire to support a variety of application connectors and integrations. Not all applications are popular enough for technology vendors to develop integration capabilities. Fortunately, Authomize is one ITDR solution which has invested in an API to allow businesses to integrate applications beyond Authomize’s own connectors.
About the Author

David Perrin is an IAM Senior Consultant with Templar Shield. He enjoys learning about customer challenges and helping them achieve their goals. David’s experience includes Enterprise and IAM System Design, application integration, system testing, and assurance. In these capacities, David helps clients realize improved efficiencies, business requirements, and customer experiences. He can be reached at david.perrin@templarshield.com.
January 11, 2023 | Author: Kanika Anand

IDENTITY AND ACCESS
MANAGEMENT IMPLEMENTATION
– BEST PRACTICES TO AVOID FAILURES
Identity management is key to ensure trust, privacy, and security as well as to facilitate collaboration and improve analytics.
– William Crowell
Former Deputy Director, Board Member
National Security Agency (NSA)
As organizations are expanding and remote work becomes a normal way of life, it is important to understand Identity and Access Management (IAM) needs and implement the required IAM solutions to reduce security threats.
Major reasons for identity related data breaches may include having an ineffective IAM program or not having one at all. A recent poll survey campaign conducted by Templar Shield shows that while most organizations have implemented an effective Identity and Access Management program, there is still a sizeable portion of organizations accounting for 25% that say they do not have an IAM program.
Also, as per a recent study by Gartner, it was discovered that 67% of respondents are aware of their identity challenges but are unsure of how to fully address it. Although 58% of respondents deemed identity management to be of utmost importance, 61% of respondents said that their company believes identity management is too time- and money-consuming to manage effectively on a continuous basis.
The importance of IAM is recognized by businesses worldwide. But while the technology is being widely adopted today, implementation has always been difficult and complex, and unfortunately remains so.
In essence, IAM thrives on striking a balance between user experience and data security. There is a greater need for reliable identity and access management solutions as systems, users, and data volumes increase. Because of their extensive trail of implementation complexities, traditional IAM products, which are intended to improve an organization’s productivity and security, have instead turned into a complicated problem for organizations.
Identity and Access Management implementations take a long time to complete (usually around 6-18 months) and often do not produce results that were promised. The complexity eventually causes the entire implementation to fail by falling short of expectations of the stakeholder executive committee.
IAM solutions have always been expensive because they have complex workflows that require an expert to carry out. If proper analysis is not conducted beforehand, these challenges can also have an impact on the schedule and budget.
Major Causes of implementation failure:
Based on experience, Templar Shield has identified a variety of factors that can contribute to the failure of an Identity and Access Management Implementation:
Lack of clear objectives – One of the first challenges that c-suite executives face is defining clear objectives. It becomes important to understand what your IAM requirements are for a successful and less complex implementation process. Common questions that must be asked as the first step may include:
Not being aware who the users are – Gone are the days when users simply included the employees and contractors of an organization. In the complex business environment today, users are not only traditional employees and contractors but also include third party vendors, bots, and external business applications. It is important to understand that every user will have a different requirement and risk profile. An IAM program will help an organization to keep track of what the user is doing and how the confidential data is being utilized. The recent SolarWinds breach was a tough reminder that technological advancements will always carry inherent risks. Managing both internal as well as external user identities is key to gaining comprehensive cyber security for any organization.
Lack of proper planning – IAM implementation is complex and resource intensive. Not planning proper resources and when business grows, not planning to meet the changes in technology and not being able to meet new demands can all lead to IAM implementation failure.
Lack of auditing – As businesses grow and move toward achieving new goals and objectives, users require different access rules to fit their new role. Here, revoking access to previously required resources must not be skipped. If not done, it can lead to a situation where users have access to apps or data that they no longer require.
Insufficient training – IAM implementation is a set of complex processes. Proper training for employees handling such complex tasks must be scheduled. They must be up to date with the technological advancements in the field and must possess necessary skills required.
Best practices for managing an effective IAM program:
Create a long-term roadmap – a successful implementation requires a long-term program which is aligned with the goals of the organization, has several phases and proper governance. It will also reveal gaps in the implementation plan. Stick to the roadmap as much as possible, but leave a little room for flexibility, as market conditions and business strategy may change.
Provide proper training to employees managing the complex implementation processes – it is important for the people involved to understand the tools well before implementation. Training should be an on-going process.
Choose your service partner wisely – depending on the organization’s objectives, choose the right service provider to ensure you stay within the stipulated time, budget and most importantly you are able to achieve the expected outcome.
Identify your end user – End users should have a strong representation in the project scope because they will be the ones most impacted by an IAM system. To ensure you comprehend how they use their various applications on a frequent basis, involve users from various departments. You’ll get a clearer idea of how they’ll have to adapt to the changes the IAM solution will bring in.
Conduct a routine inspection – it is suggested to revisit your IAM policies semi-annually. The recent poll survey campaign conducted by Templar Shield shows that 35% of organizations revisit their policies and programs every 6 months.
Every organization requires an IAM solution on some level. Part of thorough planning for a successful and efficient IAM implementation is understanding associated pitfalls and knowing how to avoid them.
To know more about Identity and Access Management implementation, contact our experts at Templar Shield – info@templarshield.com
References:
About the Author:

Kanika Anand is an IGA Consultant at Templar Shield. She works with clients to understand their requirements and build roadmaps for effective IAM/ IGA program implementation.
For more details, please reach out to:
Frank Wray – Director, IAM Practice
Email: frank.wray@templarshield.com
March 05, 2022 | Author: Ravi Neriyanuri
In today’s digital world, organizations need to modernize the identity governance and administration (IGA) program to deal with an increased security risk exposure as the infrastructure and applications move into the cloud. In addition, the remote working and remote access to the environment have pushed the needle further to the wall.
To minimize the risk, Cybersecurity is shifting the focus beyond protecting the network, application, and data to managing & monitoring the internal/external identities that have access to the environment by securing and mapping the identities to protect the assets. Thus, IGA is becoming a fundamental and critical capability of any cybersecurity program.
In addition, the gaining adoption of Zero Trust principles, i.e., never trust, always verify, and the Password-less Authentication, are not effective unless the organization has a robust IGA program in place.
However, before reimagining the IGA program, the organizations, at the minimum, need to try to find answers to the following –
Role of Technology:
Technology plays a critical role in building, sustaining, and determining the success of the IGA program. The key to unlocking the benefits lies in selecting and implementing an IAM platform that can meet the business requirements and is technically viable and within budget. Also, It should support the various systems and technologies both on-premise and on the cloud.
Before selecting and implementing a platform to secure the identities and maintain governance, the organization must evaluate and choose a solution with built-in workflows for smoother approval, improving efficiency, and approving access reviews to protect all human and machine identities. Further, the chosen platform/technology should provide required access through an additional factor of authentication based on context, zero trust for all users, and managing access to assets either in an on-premise or cloud environment. In a nutshell, An IGA tool should provide the following capabilities:
Recommended Approach to modernize your IGA program –
For a successful IGA implementation, it is essential to look at how the current IGA program requirements are managed and follow the below-recommended approach to reimagine your IGA program.
Step 1 – Understanding the current maturity of the current IGA program helps the organization define its IGA strategy and roadmap to define and phase the entire program and, more importantly, select the right IGA product.
Step 2 – Jumpstart your IGA program with a pilot to understand and evolve the data model in the current environment to get a clear understanding of the IGA requirements.
Step 3 – After setting up the product, perform birthright access provision and build the necessary integrations.
Step 4 – Perform Request approvals and workflows for maximum end-user adoption
Step 5 – Perform the application onboarding process
A successful IGA solution or program leads to benefits like reduced operational costs, improved compliance, better audit performance, Automated and efficient user access to assets, scalable process, and reduced risks. It is required to adopt an efficient, incremental, and iterative approach for implementing IGA by collaborating between various stakeholders and it requires considering IGA maturity, people, process, and technology.
The Templar Shield Advantage
Templar Shield, Inc. is a premier cybersecurity, privacy, risk, and compliance technology professional services and value-added reseller firm. We provide various service options to meet our client’s specific needs, including advisory, integrated risk transformation, consulting, operations, and technical solutions. As part of the Identity and Access Management Service Offering, Templar Shield provides Advisory, Implementation, Integration, and Managed Services to meet our client’s short-term and long-term program management needs.
With a global delivery model and strategic partnerships with industry-leading IAM product vendors, Templar Shield helps organizations reimagine their identity governance and administration programs to strengthen security initiatives.
About the Author:

Ravi Neriyanuri is a Managing Director and Heads IAM practice at Templar Sheild. He has 26+ years of progressive experience advising global majors/fortune 500 companies on IAM strategy, program development, and technology implementation. Ravi led products development in Enterprise Security and Information Risk Management areas, is an advisor thought leader and has decades of experience in Delivery Management, Presales, Enterprise Architecture, Product Management, Risk Management, Competency building, Practice Building, and Incubation.
For more details, please reach out to:
Frank Wray – Director, IAM Practice
Email: frank.wray@templarshield.com
Introduction
January 17, 2022 | Author: Jasen Dill
On March 11, 2020, the World Health Organization declared the novel Coronavirus (COVID-19) a Global Pandemic forcing business enterprises to change their business operating model to overcome the hurdles and minimize the impact on their organization. One of the many hurdles that required the business’s attention and action was ensuring the viability of their Third-Party/Vendor ecosystem.
During these challenging times, it was not only organizations with a less-than-mature Third-Party Risk Management (TPRM) program that struggled to respond to the pandemic. Even organizations with more robust TPRM processes had to scramble as the situation demanded them to expand, enhance, modify, and improve their existing TPRM program.
Key Challenges
As the pandemic raged on, organizations successfully worked out with their vendors on reduced Service Levels and invoice processing requirements as good-faith agreements between strategic partners. However, they faced the challenge of meeting their compliance obligations and the need for protecting and safeguarding sensitive information from increasing cyber-attacks/data breaches.
Key Lessons Learned
As we leap into 2021 and the pandemic continues to challenge all of us on multiple levels, there are opportunities for business enterprises to use “2020-hindsight” to review the changes made, evaluate those changes, and incorporate them into the new standard processes.
At Templar Shield, we have been supporting our clients on their third-party risk management program journey. Our unique TPRM managed services model provided us an opportunity to work closely with our clients, helping them overcome the challenges posed by the COVID pandemic. We observed that the companies that we’re able to pivot quickly benefitted. Here are some of the key lessons learned.
Changed Third-Party Risk Landscape:
Program Maturity is the Key:
Extended Program Coverage:
Third-Party Risk Management teams saw an increase in day-to-day responsibilities –
Revised Assessment Methodology/Approach:
Continuous Monitoring:
Extended Support/Co-Services Model:
This additional workload strained even the most seasoned organizations as companies scrambled for ways to pivot themselves to the “new norm.”
Conclusion
As we continue to maneuver through life, during a Pandemic or not, managing vendors will not become any less important ever.
What the pandemic has allowed us to do is apply the lessons we learned to mature third-party risk management programs and give our strategic partners the much-needed assistance to manage their third parties, keep data secure, and maintain regulatory compliance.
About Templar Shield
Templar Shield is a premier information security, risk, and compliance technology professional services firm. We provide various service options to meet our client’s specific needs, including advisory, integrated risk transformation consulting, operations, and technical solutions. We have partnered with over 100 Fortune 1000 companies and government entities to implement innovative integrated risk and compliance solutions across organizations.
Our Third-Party Risk Management Services & Solutions
At Templar Shield, we provide end-to-end services and solutions to meet your unique third-party risk management requirements. Our seasoned TRPM domain specialists and technology consultants can help you with –
We leveraged years of rich experience gained from helping organizations build their TPRM programs and developed a unique TPRM managed services model allowing clients to choose from a selection of “a la carte services” to meet their program management requirements.
The TPRM managed services model allows you to spread the workload and segregate at any process step. This, in turn, allows you to focus on addressing bigger core issues and maturing the TPRM program.
About the Author

Jasen is a seasoned GRC Consultant with cross-sector/industry and multi-domain expertise in providing consulting and advisory services. Jasen’s experience includes a diverse portfolio of innovative technology implementations and program transformations to support his clients’ strategic priorities. In this capacity, Jasen leads TPRM Program Managed Services and helps clients design, architect, and implement solutions to automate their TPRM programs, especially on tools such as RSA Archer, ServiceNow, Lockpath, IBM OpenPages, BlackKite, Rapid Rating, RiskRecon, and the like.
He can be reached at jasen.dill@templarshield.com.